Codefest'19 CTF Writeups
The Capture the Flag event for Codefest’19 was hosted from 8 pm, 23rd August 2019 to 12 noon, 24th August 2019 on Hackerrank.
The contest link can be found here. There were a total of 1532 registrations and 518 people who were successful in solving atleast one challenge.
So, onto the writeups.
Welcome to Codefest 19! (Intro Challenge — 100pts)
This was the introductory challenge. I had tried to make it a bit difficult than the normal introductory challenges, but I felt that it proved to be a bit difficult for the beginners.
Here, first you had to join the telegram group linked in the proble. There you got the first half of the flag — CodefestCTF{G3t_r3ady_. For the other half there was a pinned message on the group.
The other half of the flag was uploaded on the contest page yesterday by accident. It has now been removed. Can you find it?
For this you had to use archive.org, there was a snapshot of the contest page created on 23rd Aug 2019. Viewing the snapshot got you the second half of the flag —f0r_C0def3stCTF-8fb34fjr4bs43ur8}.
So, the final flag is — CodefestCTF{G3t_r3ady_f0r_C0def3stCTF-8fb34fjr4bs43ur8}
What language is this? (Misc — 100pts)
This was basically a esoteric language question. The given text was —
iiisdsiiioiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiodddddddddddoioiodoiiiiiiiiiiiiiioiodddddddddddddddddddddddddddddddddddddddddddddddddoiiiiiiiiiiiiiiiiioddddddddddddddoiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiioddddddddddddddddddddddddddddddddddddoiiiiiiiiiiiiiioiiiiiiiodddddddddodddddddddddddddddddddddddddddddddddddddddddddddddddoddddddddddddddddddddddddddddddddddddddsiiiiiiiiioddddddddoddddddoiiiiiiiiiiiiiiiiiiiiioddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddoddddddddddddddddddddddddddddddddsiiisisdddddoddddddddddddddddddddddddddddodddddddddddddddddddoddddddddddddddddddddddddddddddddsiiisisoioiodoiiiiiiiiiiiiiioiodddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddoiiiiiiiioddddddddddddddddddddddddddddddddddddddddddddddsiiiio
The language was Deadfish. You could use an online decoder for that language, something like this.
The final flag was — CodefestCTF{Welc0me_t0_C0defest19}
Gibberish file (Misc — 100pts)
The hint was in the problem statement. You had to reverse the file to find the flag. A simple one-line script could do it
open("output2.txt", "wb").write(open("output.txt", "rb").read()[::-1])
The resulting had some text like
𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ 𝝩𝗵𝙚 𝗳𝒍𝙖𝗴 𝒊𝙨 𝐋𝒊𝐓𝚬𝐫𝚨𝐋﹏𝕽𝜠𝓥Eℜ𝕊𝐢𝙣𝓖ꓸ
The flag was the ASCII analog of each unicode character.
The flag was — CodefestCTF{LiTErAL_REVERSinG}
Image Corruption (Forensics — 100pts)
In the challenge, you were given a link to a corrupted .bmp file. On viewing the file in a hex editor, and also checking the magic bytes —
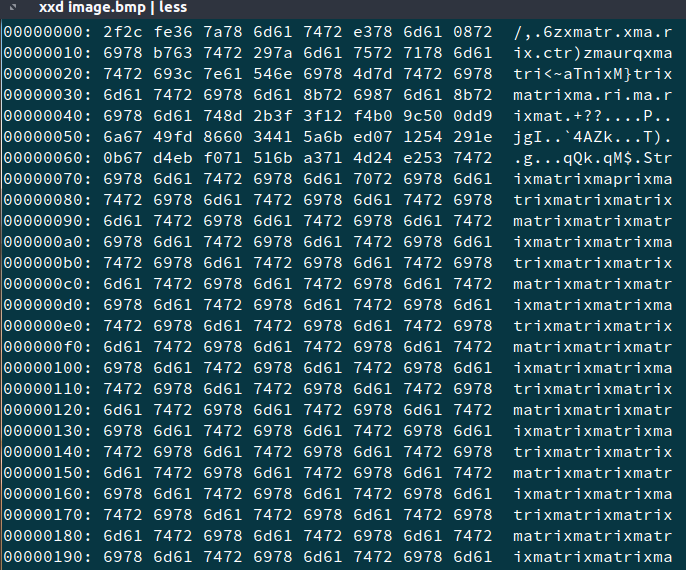
We know there is something to do with “matrix”. Also for a normal .bmp file the initial magic bytes are 424d 8a44 1300. XORing this with the first six bytes of the given file also gives you “matrix”. So to solve the challenge, we XOR the whole image with “matrix”.
Run the script, and you obtain the correct file.
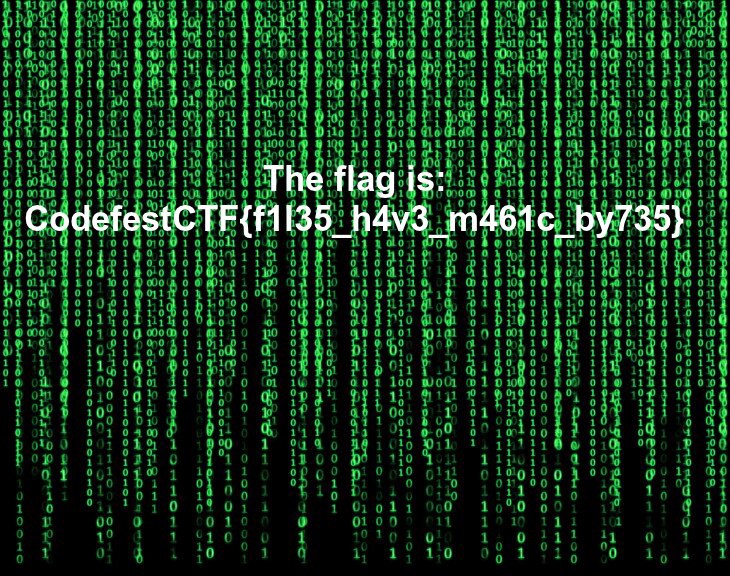
The flag is — CodefestCTF{f1l35_h4v3_m461c_by735}
Mail capture (Steganography— 100pts)
You are presented with a “email friendly text”. This was encoded to unicode by a tool called uuencode. It can be decoded by using uudecode, a decoder for such formats. Running uudecode with the file gives an output file called “flag_encoded”. The contents are the flag — CodefestCTF{7h15_15_4_c001_3nc0d1n9}
Cats are innocent, right? (Steganography— 500pts)
This challenge was based on LSB steganography. I had used a tool called stegify.
The challenge image -

On running the command -
stegify -op decode -carrier cute_kittens.jpg -result hello
We get a hello.zip file which was embedded in the LSBs of the image. The zip file had a file inside it but that was of no use. The flag was appended at the end of the zip file.
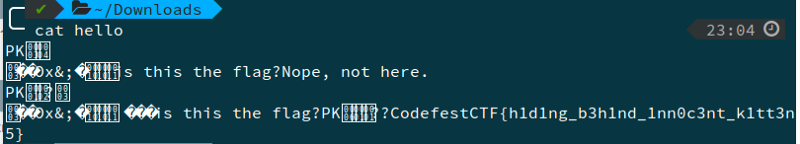
The flag is appended at the end of the zip file
The flag is — CodefestCTF{h1d1ng_b3h1nd_1nn0c3nt_k1tt3n5}
Weird encoding (Misc— 200pts)
We are given the following “encoding”
0x85+1x1+0x14
0x7+1x1+0x7+1x1+0x9+1x2+0x3+1x4+0x3+1x1+0x6+1x5+0x1+1x1+0x2+1x1+0x1+1x2+0x13+1x2+0x3+1x1+0x8+1x1+0x5+1x2+0x8
0x1+1x5+0x18+1x3+0x3+1x1+0x16+1x2+0x1+1x1+0x5+1x2+0x2+1x1+0x3+1x1+0x4+1x2+0x3+1x3+0x3+1x1+0x2+1x2+0x4+1x3+0x8
0x3+1x1+0x7+1x1+0x11+1x2+0x1+1x1+0x3+1x5+0x12+1x1+0x2+1x1+0x7+1x1+0x10+1x1+0x3+1x2+0x1+1x1+0x5+1x3+0x4+1x1+0x1+1x2+0x2+1x1+0x4
0x3+1x1+0x3+1x1+0x7+1x2+0x3+1x1+0x2+1x1+0x2+1x1+0x7+1x1+0x11+1x2+0x2+1x2+0x5+1x2+0x10+1x1+0x3+1x1+0x2+1x1+0x3+1x2+0x2+1x1+0x4+1x4+0x7
0x3+1x1+0x3+1x1+0x3+1x1+0x1+1x3+0x10+1x1+0x7+1x1+0x7+1x1+0x3+1x1+0x3+1x1+0x1+1x2+0x2+1x3+0x8+1x5+0x4+1x1+0x3+1x9+0x1+1x3+0x7
0x3+1x1+0x3+1x3+0x1+1x1+0x1+1x4+0x9+1x1+0x6+1x2+0x2+1x1+0x7+1x2+0x3+1x1+0x2+1x1+0x4+1x1+0x10+1x1+0x6+1x1+0x7+1x1+0x7+1x4+0x4
0x5+1x1+0x1+1x1+0x1+1x1+0x1+1x1+0x4+1x2+0x7+1x2+0x3+1x4+0x11+1x1+0x4+1x1+0x2+1x1+0x3+1x2+0x6+1x1+0x3+1x1+0x6+1x1+0x7+1x1+0x1+1x1+0x1+1x5+0x7
0x7+1x1+0x1+1x1+0x1+1x1+0x2+1x3+0x7+1x5+0x16+1x1+0x4+1x1+0x2+1x1+0x1+1x3+0x3+1x6+0x2+1x1+0x2+1x1+0x1+1x5+0x5+1x1+0x2+1x1+0x4+1x1+0x7
0x18+1x5+0x13+1x6+0x27+1x1+0x14+1x1+0x2+1x2+0x2+1x1+0x5+1x1+0x2
0x1+1x1+0x5+1x1+0x4+1x1+0x3+1x1+0x8+1x1+0x8+1x1+0x9+1x1+0x8+1x1+0x5+1x1+0x17+1x1+0x10+1x3+0x9
0x68+1x1+0x11+1x1+0x19
Here a bit of observation was required to figure out that the “x” symbol mean concatenation n number of a character, like 0x5 will mean 00000. And “+” would mean concatenation of two strings of different type. Also, one will also have to decide on 0 representing 255 255 255 i.e. the color white and 1 representing 0 0 0 , i.e. the color black. You could have experimented with both combinations but eventually you would get the correct mapping.
The following script can help generate the image.
The obtained image is this -
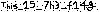
The flag is — CodefestCTF{This_15_7h3_f14g}.
Linux RE 1 (Reversing — 300pts)
This challenge was a bit difficult to solve using a debugger due to some anti-debugging techniques that were implemented. Also, initially the ELF was packed using UPX, which was visible as a string when you would have run the strings command. So, first use
upx -d
with the ELF to decompress it.
For the next part, You could use a disassembler or a decompiler to get the source code and eventually reverse the binary. The executable was generated from a C++ file hence it was a bit messy to view in a decompiler.
The decompiled view (using Ghidra) of the main function (the interesting part) is the following -
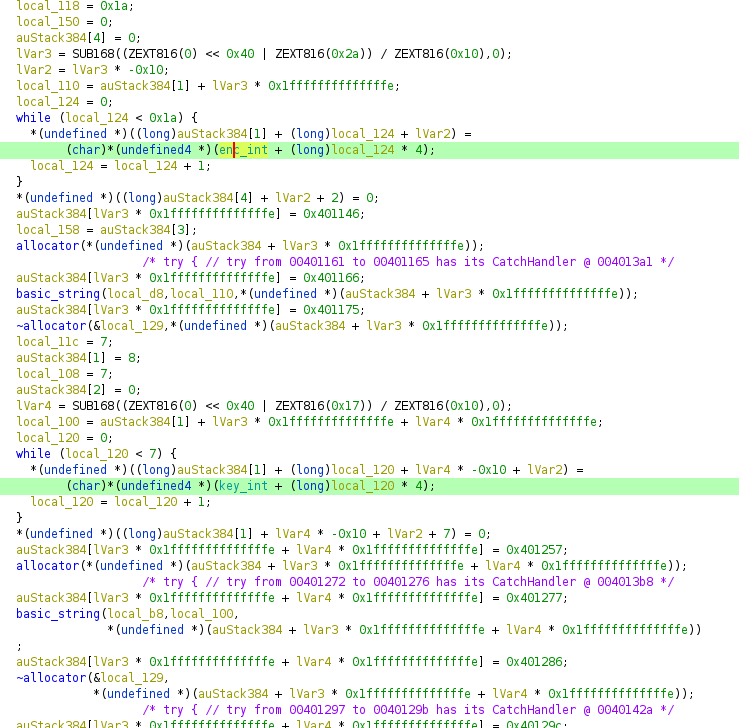
The key_int and enc_int are global variables. The main logic of the ELF is in the rahasya function.
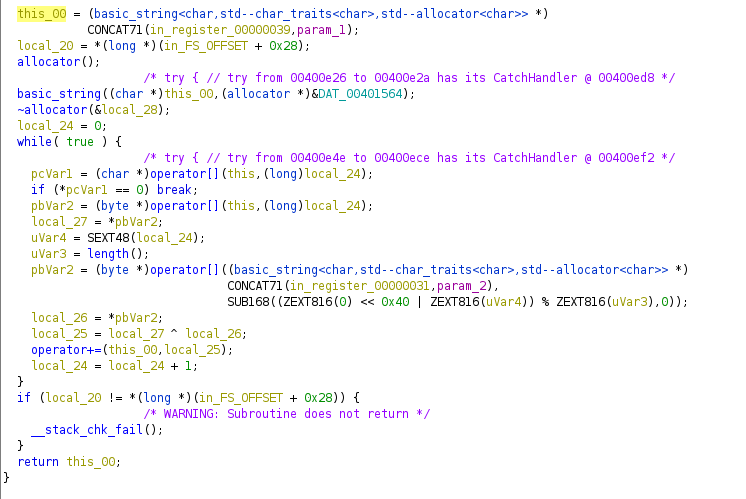
This basically takes two strings and XORs them and returns the XORd string. The two strings it takes as input are the user input and the key_int string. The XORd data is matched with the enc_int data.
So, basically to reverse the binary you have to XOR both the key_int and enc_int data.

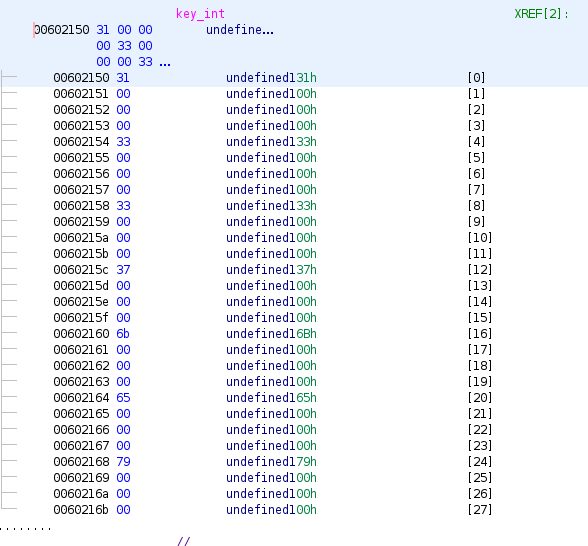
Basically,
int enc_int[] = {80, 93, 3, 67, 3, 86, 11, 110, 64, 2, 90, 27, 84, 28, 110, 75, 3, 69, 52, 6, 11, 5, 80, 88, 90, 88};
int key_int[] = {49, 51, 51, 55, 107, 101, 121};
XOR both of them, and you get an0th3r_s1mp1e_x0r_cr4ckm3
So, the flag is CodefestCTF{an0th3r_s1mp1e_x0r_cr4ckm3}
Linux RE 2 (Reversing — 500pts)
Again we open the file in IDA or any disassembler and/or decompiler we see that the input should satisfy a set of conditions on the letters of the input.
The conditions can be translated as
We can use some kind of SMT solver like z3 to find the password.
The obtained password is — shouldve_used_some_tool
The flag, hence, is CodefestCTF{shouldve_used_some_tool}
Windows RE (Reversing — 500pts)
In this problem, the Windows exe file (actually a .NET file) that was provided, was packed with ConfuserEx. We can use NoFuserEx, which is a free deobfuscator for this packer.
Then, open the executable in any .NET decompiler like dnSpy and check the Form function to get the password as well as the flag.
Password — thisisa1337password
The flag — CodefestCTF{51mp13_1npu7_v411d4710n_8u7_w17h_4_7w157}
No Fatshaming (Web — 600pts)
I’ll cheat a bit here xD. You can read my friend Yashit’s awesome writeup on the challenge.
Flag is — CodefestCTF{1AmTeHHHAX00Rr4uj8rfi4e$%y5yhrf}
Hope you had a great time solving the challenges and that it was a good learning experience for beginners.